Introducing Cloak, the Privacy Validium
Oct 14, 2025 · 4 min read
Introducing Cloak, the Privacy Validium
tl;dr
Cloak brings privacy by default to the EVM with ZK proofs, while staying compatible with existing tooling. Its RPC Proxy keeps user data confidential and enables fine-grained, auditable access and controlled disclosures for regulators. Together, these features enable privacy in an institution-friendly Web3 environment.
While EVM technology continues to experiment and deliver new use cases, it still hasn’t reached mainstream adoption for everyday transactions. The main reason is the lack of privacy, a non-negotiable requirement especially for use cases involving regulated institutions. Today, robust and compliant privacy is still a missing piece of Web3’s core infrastructure.
To address this, Scroll is introducing Cloak, the Privacy Validium.
Announced in August 2025, Cloak enforces privacy by default while guaranteeing state correctness through ZK proofs that reveal no user data. At the same time, it supports institutional auditability through controlled disclosures, enabling regulators or authorized parties to access data only when required.
Below is a concise look at the protocol’s architecture and how it balances user confidentiality with institutional needs. Let’s begin with the Cloak RPC Authentication Proxy, the protocol’s most important piece.
What is Cloak’s RPC Proxy?
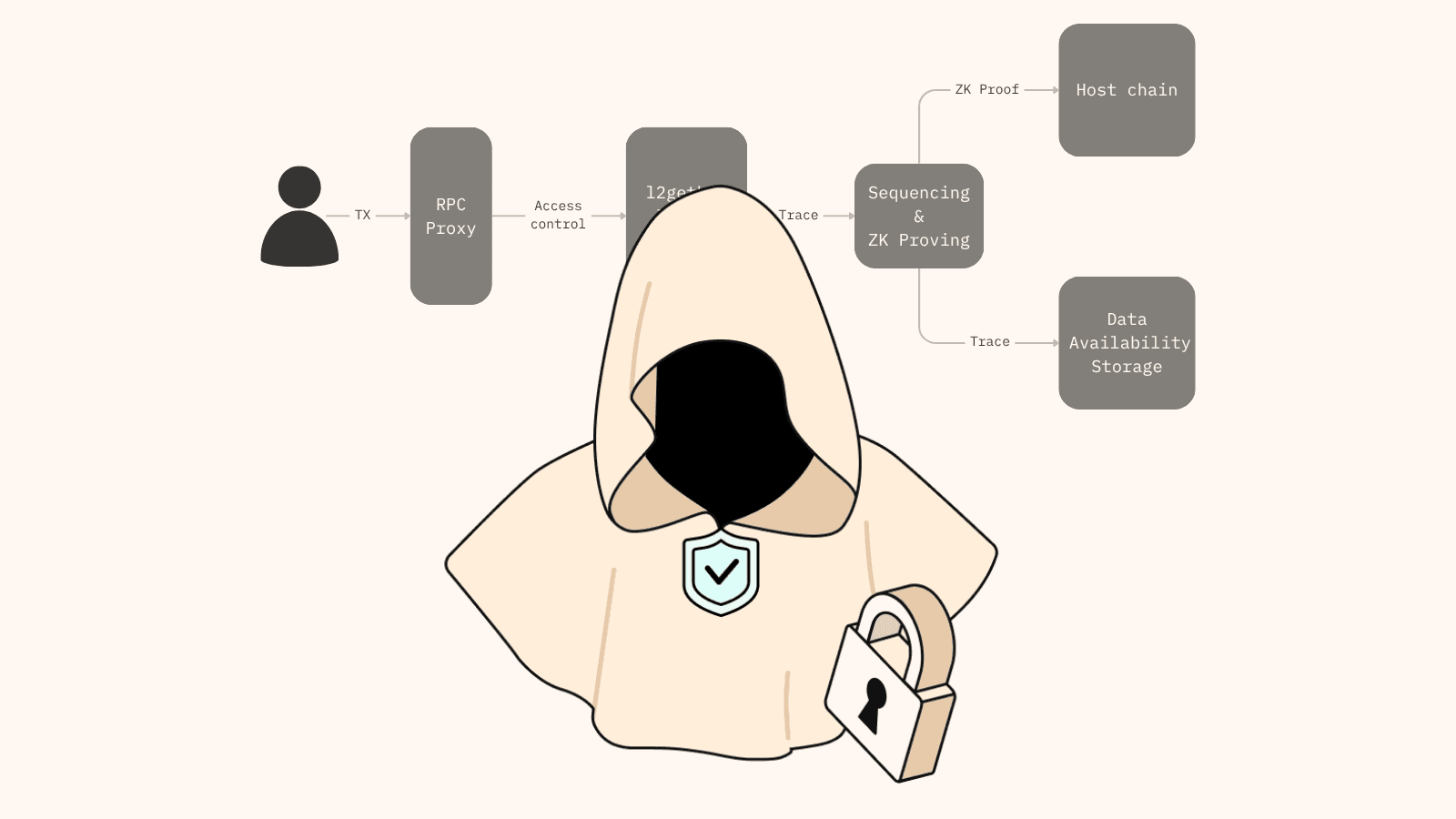
The RPC Proxy is an intermediary layer between users and EVM nodes, designed to reuse battle-tested EVM tooling: developer toolchains, wallets, indexers, multi-node infrastructure, audited smart contracts, and Scroll’s ZK validation stack.
By sitting between users and nodes, the RPC Proxy preserves standard EVM behavior. This means that, from the user and developer's point of view, it looks and feels just like an EVM node with standard RPC commands. However, it manages user access to information by enforcing privacy and revealing authorized data only.
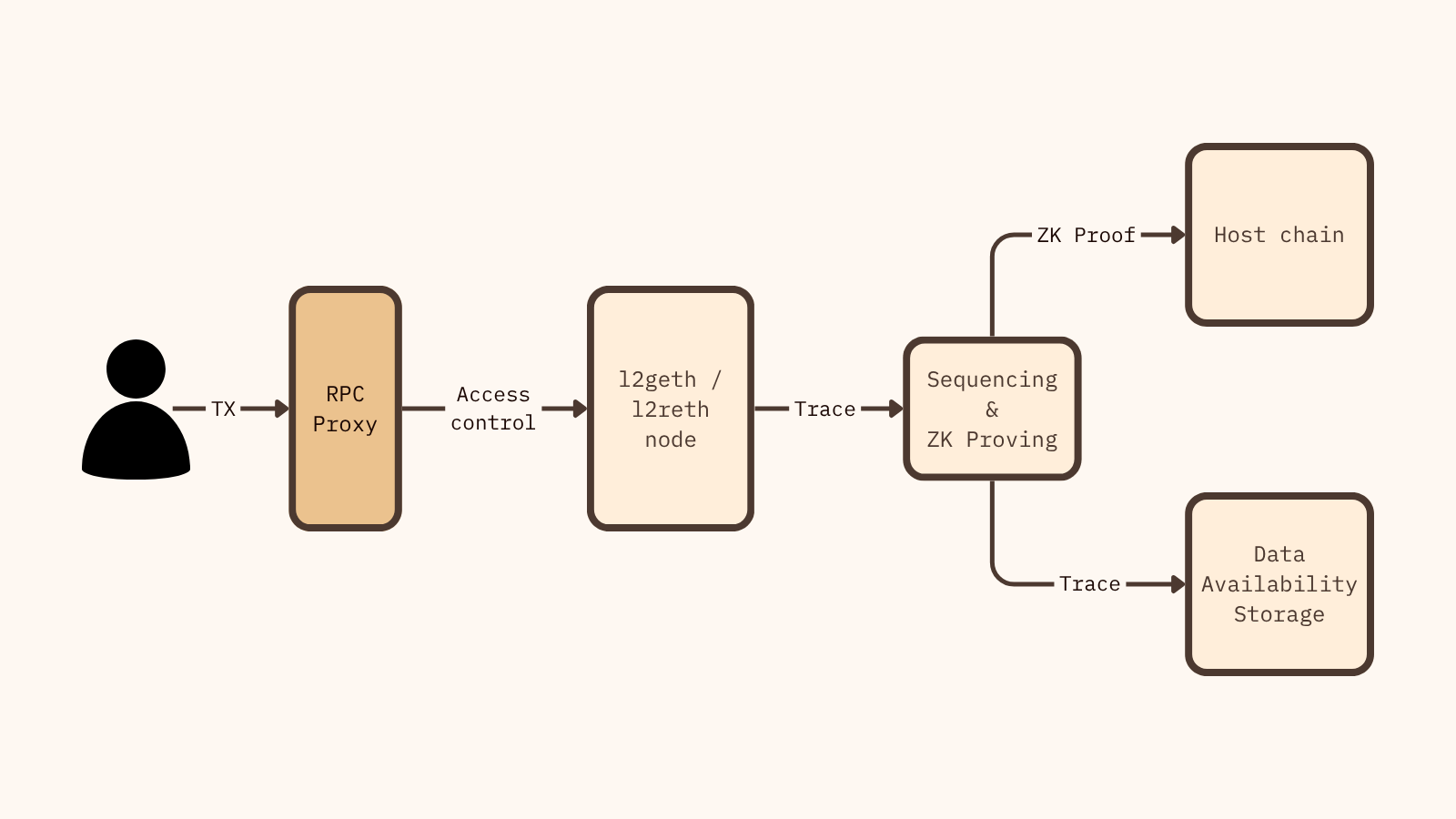 Notice how users interact with the RPC Proxy only, instead of interacting with the L2 nodes directly.
Notice how users interact with the RPC Proxy only, instead of interacting with the L2 nodes directly.
In most cases, users interact with a Cloak chain by signing in with an EVM wallet and receiving from the RPC Proxy a scoped access to account data.
Step by step typical interaction
When a user visits a dApp deployed on Cloak, the first step is proving ownership of their account by signing an EIP-4361 SIWE message with their EVM wallet. The RPC Proxy receives this signature and responds with a JWT (JSON Web Token), starting a standard authentication process.
This token defines granular permissions. In the most common case, it grants read-only access to balances and transaction history, as well as the ability to send transactions from that account. The JWT is then appended to any transaction or RPC call made through familiar libraries like ethers.js, web3.js, or viem.
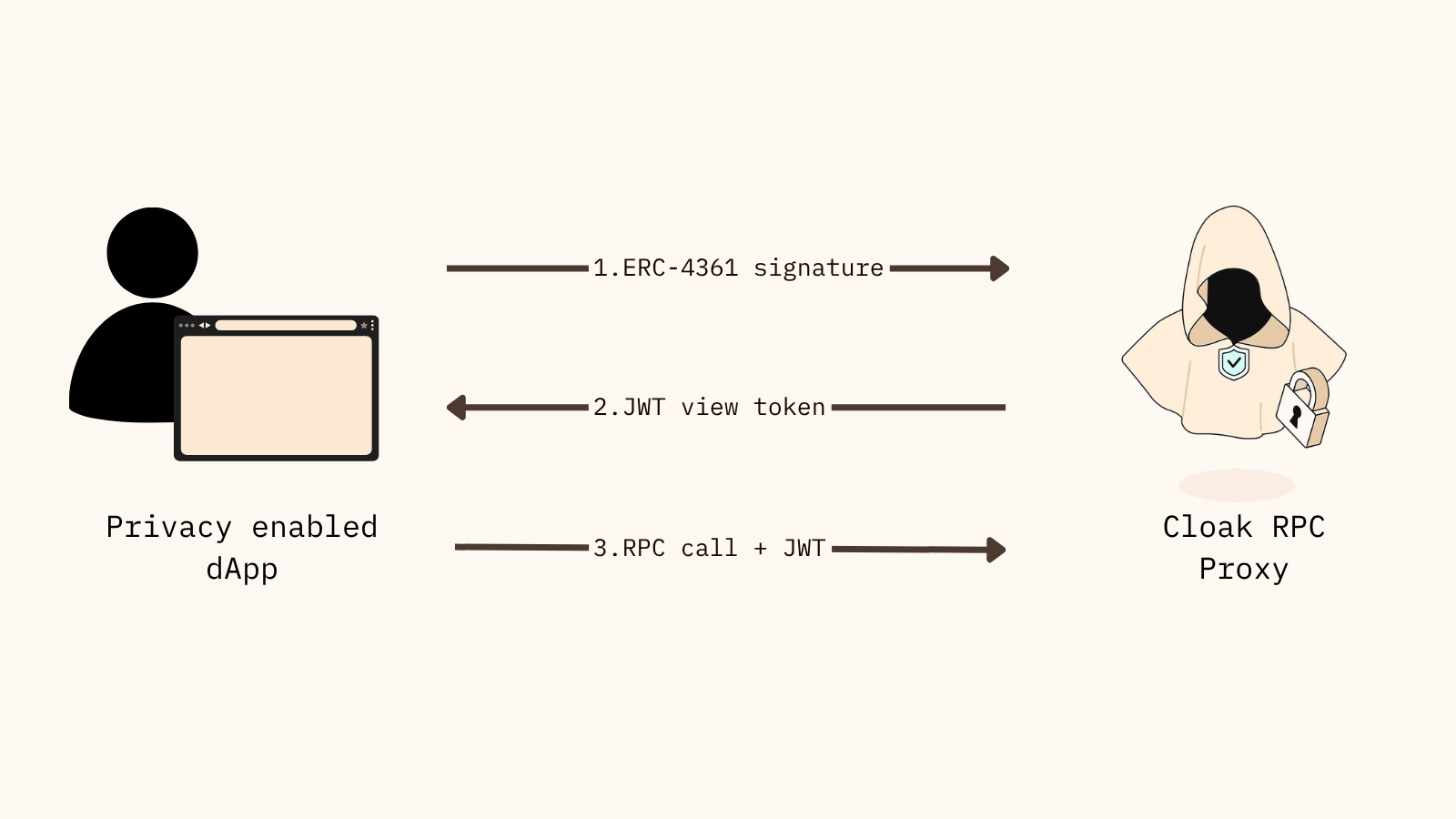 Step by step user interaction with a privacy enabled dApp running on Cloak.
Step by step user interaction with a privacy enabled dApp running on Cloak.
Because users never access nodes directly, the protocol can apply different levels of access control depending on the chain’s purpose and its compliance requirements. It can provide viewing keys for protocol-level audits, or enable controlled disclosure for investigations involving specific users or assets.
About Data Availability
Fast, cheap and fully EVM compatible privacy is only possible in validiums and not rollups. This means that Cloak ledger data is not posted to the host chain, i.e. unlike rollups there is no protocol-enforced data availability.
To function, Cloak needs a trusted party such as a regulated institution or a Data Availability Committee to serve as the operator. This operator is tasked with running the EVM nodes, prover, and sequencer. Their primary duties are to maintain data confidentiality and submit ZK proofs to the host chain to guarantee the correct execution of all transactions.
It’s important to mention that posting the transaction history on the host chain is not a technical necessity of ZK. While the vast majority of current ZK Layer 2 chains publish traces on the host chain to guarantee liveness and permissionless withdrawals, Cloak ZK verification only requires a commitment to it’s new ledger and the mathematical proof to validate the correctness of the state transition.
Cloak is open source and currently under active development. To learn more, visit the Cloak docs. If you’d like to start a conversation with the Scroll team, please fill out this form.